✔ Governance as Code — How Policy Moved from PDF Manuals to Pipelines 👈
🔑 Executive Summary
Once upon a time, governance meant documents — thick binders of policies and PDF manuals that guided developers through checklists and review boards. As systems scaled and delivery cycles accelerated, that model broke down. Governance needed to evolve from oversight to automation.
Governance as Code transforms policy from static documentation into executable logic that lives inside the CI/CD pipeline. By combining OpenAPI 3.1, Spectral, decK, and OPA/Rego, organizations can automate compliance, version-control their policies, and synchronize design, policy, and runtime — creating what Ea-2-Sa calls a living governance fabric.
📜 From SOA to API: The Governance Bottleneck
During the early days of Service-Oriented Architecture (SOA), governance acted as a gatekeeper. Manual review boards, static UDDI registries, and lengthy approval cycles ensured compliance — but slowed delivery. As APIs and microservices proliferated, these bottlenecks became unsustainable.
Lesson learned: Governance without automation leads to fragmentation. APIs demanded speed, agility, and policy that could move as fast as code.
🧩 The Rise of Declarative Design
The breakthrough came with OpenAPI — a way to describe an API as data. A single YAML file became the blueprint, validation engine, and the language of alignment between teams. Yet governance still existed outside the lifecycle — reviewed in meetings, enforced manually, and forgotten after deployment.
Policy-as-Code changed that. Borrowed from infrastructure automation, it moved policy enforcement directly into pipelines. Compliance checks could now run automatically on every commit, turning governance from a gate into a guardrail.
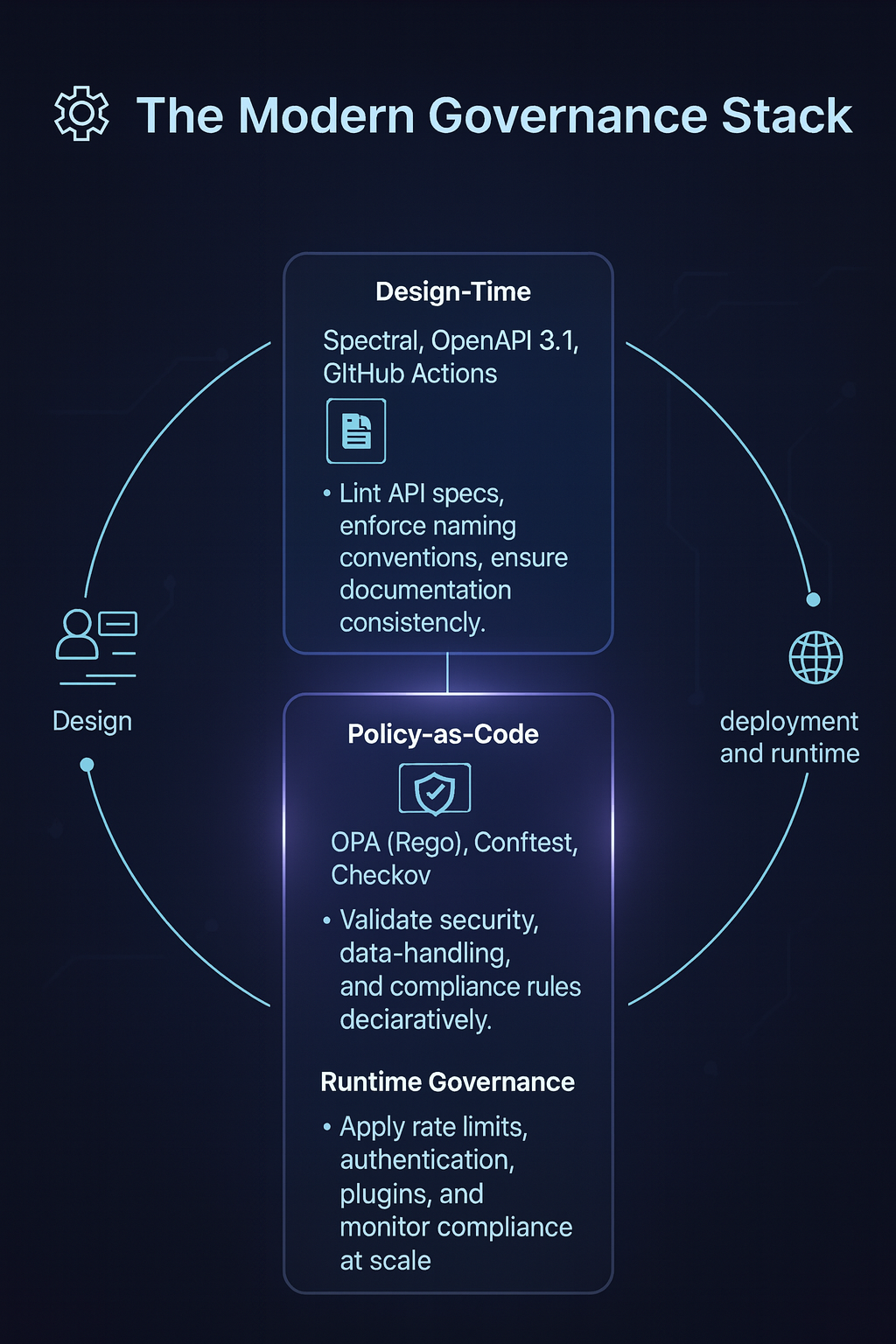
⚙️ The Modern Governance Stack
Modern API organizations use a three-layered governance stack that unites design, policy, and runtime into one continuous system:
| Layer | Tooling | Purpose |
|---|---|---|
| Design-Time | Spectral, OpenAPI 3.1, GitHub Actions | Lint API specs, enforce naming conventions, ensure documentation consistency. |
| Policy-as-Code | OPA (Rego), Conftest, Checkov | Validate security, data-handling, and compliance rules declaratively. |
| Runtime Governance | Kong Gateway, decK, ArgoCD (GitOps) | Apply rate limits, authentication, plugins, and monitor compliance at scale. |
🔄 From Manual Compliance to Continuous Assurance
Governance is no longer a meeting — it’s a metric. Every change in an OpenAPI specification triggers automated checks:
- Design validation: Spectral linting ensures consistency and completeness.
- Policy enforcement: OPA and Conftest validate security and compliance logic.
- Runtime sync: decK and ArgoCD deploy updates declaratively to Kong Gateway.
The result is continuous assurance — compliance that runs alongside delivery, not behind it. Every rule is testable, every change traceable, and every deployment reproducible.
🏛 The Architectural Significance (Ea-2-Sa Perspective)
From an Enterprise Architecture viewpoint, Governance as Code operationalizes what TOGAF calls Architecture Principles. Policies are no longer abstract; they are executable. In the Ea-2-Sa framework, this convergence aligns the three foundational domains:
- Process: CI/CD pipelines encode compliance and approvals.
- Technology: Gateways and automation enforce consistent behavior.
- People: Architects evolve from reviewers to policy authors and curators.
This integration turns governance from an overhead into a value-stream enabler, merging agility with accountability.
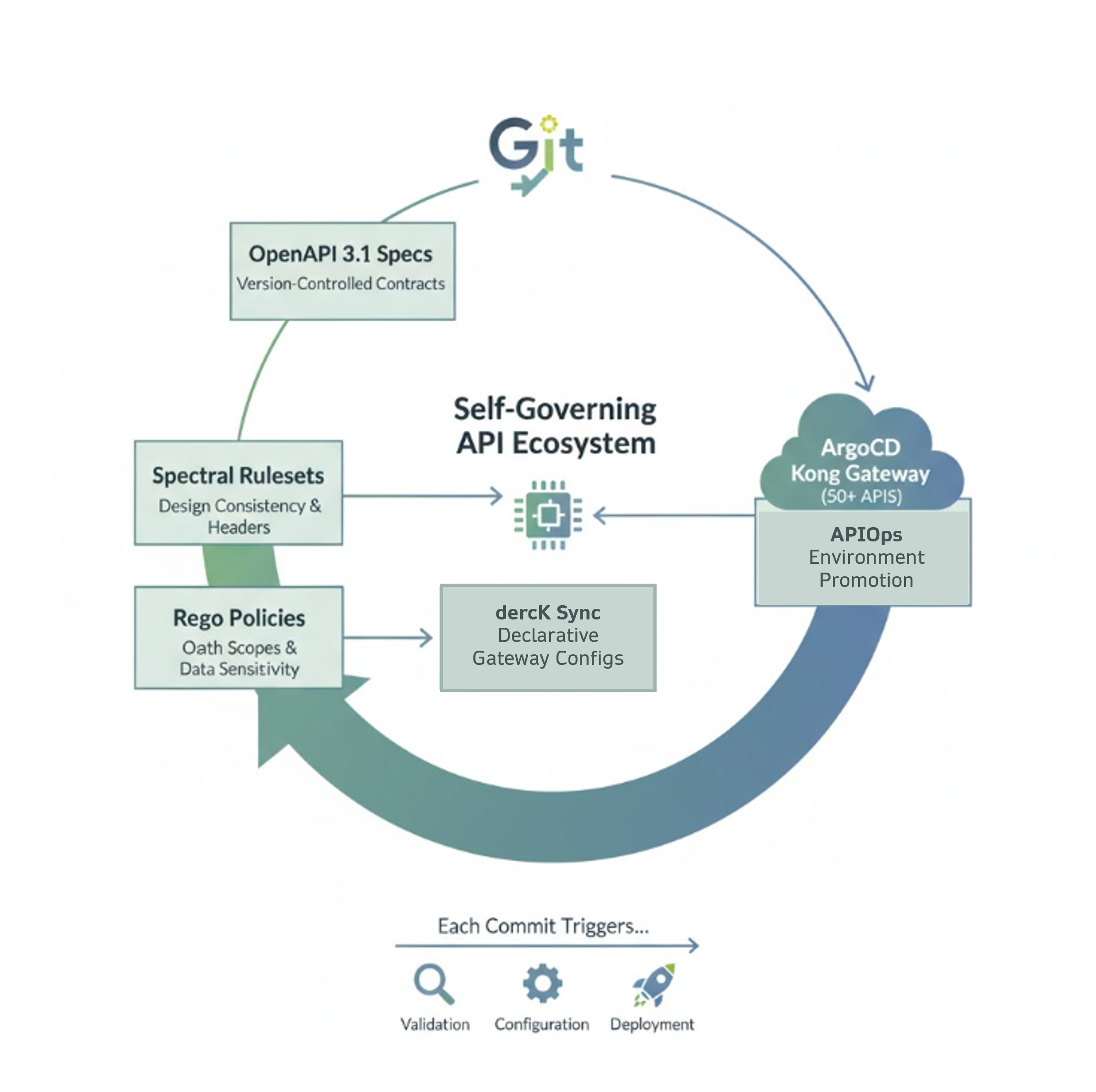
🧠 Practical Implementation Example
Scenario: Your organization manages 50+ APIs using Kong Gateway. A Governance-as-Code pipeline might look like this:
- OpenAPI 3.1 specs stored in Git as version-controlled contracts.
- Spectral rulesets enforce design consistency and required headers.
- Rego policies validate OAuth scopes and data sensitivity levels.
- decK sync pushes gateway configs declaratively.
- ArgoCD automates environment promotion via GitOps.
Each commit triggers validation, configuration, and deployment — creating a self-governing API ecosystem.
🔮 Looking Ahead: Governance in the Agentic Era
As AI agents and machine learning models begin consuming APIs autonomously, the need for automated, trustworthy governance grows. Future gateways like Kong Konnect and frameworks like OpenMeter will extend policy enforcement into model observability, token metering, and AI-driven security analytics.
In this agentic era, Governance as Code becomes the foundation of digital trust — allowing agents, APIs, and humans to operate within the same governed fabric.
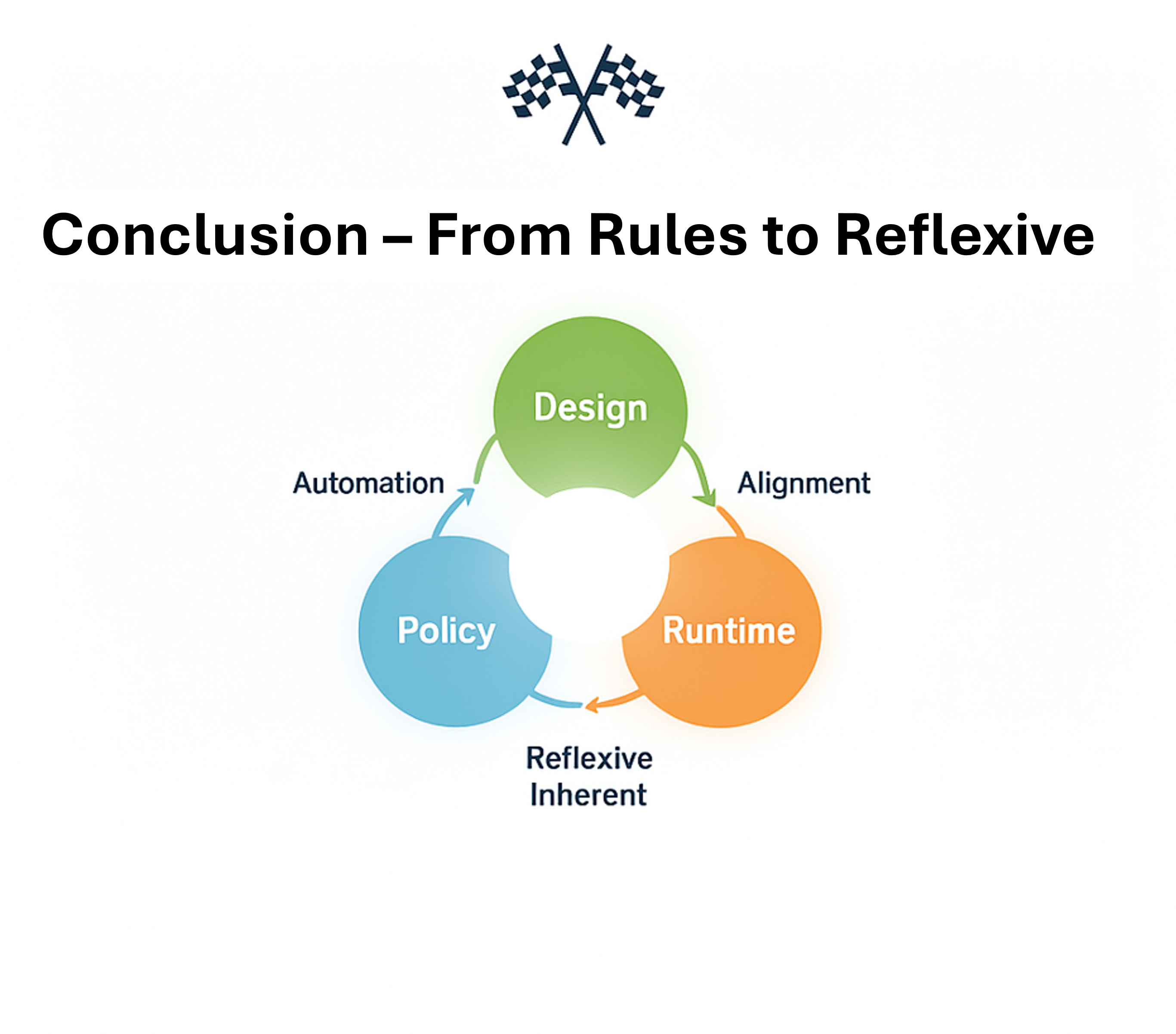
🏁 Conclusion — From Rules to Reflexes
The greatest success of Governance as Code isn’t automation; it’s alignment. When design, policy, and runtime converge, governance becomes reflexive — an inherent property of the system rather than an afterthought. Enterprises that achieve this fusion will deliver software faster, safer, and with measurable trust.