✔ Part 2 — From OpenAPI 3.1 to Policy-as-Code with Kong and GitOps 👈
🔑 Executive Summary
In Part 1 — The Blueprint, we established the contract-driven foundation using OpenAPI 3.1 and the Design → Mock → Code methodology. Now, in Part 2, we move from blueprint to execution — showing how to operationalize your API contracts through Kong Gateway, decK, and GitOps.
The goal: create a fully automated pipeline where API specifications drive configuration, governance, and runtime behavior — a practical realization of Policy-as-Code in API management.
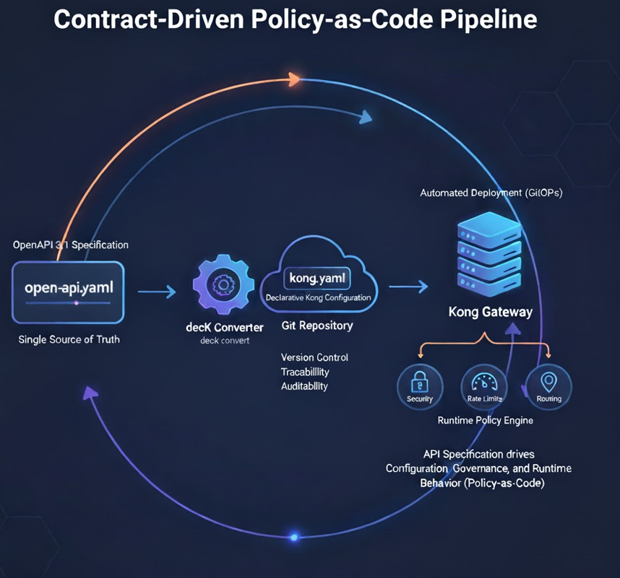
🧭 Step 1 — Linking OpenAPI to Kong Gateway
Kong Gateway acts as the runtime policy engine for your APIs. With decK (Declarative Configuration for Kong), you can import an OpenAPI 3.1 spec and automatically generate services, routes, and plugins.
deck convert --from openapi --input openapi.yaml --output kong.yaml- Services & Routes: Each OpenAPI path and method is mapped into a Kong route.
- SecuritySchemes: Automatically become
key-auth,jwt, oroauth2plugins. - Rate Limits & Validation: Added declaratively through rate-limiting and request-validator plugins.
This conversion bridges the design-time contract and the live gateway configuration — the first link in your Policy-as-Code chain.
⚙️ Step 2 — Version Control with Git
Both your openapi.yaml and kong.yaml live in the same repository.
Each branch, commit, or tag represents a unique version of your API contract and corresponding gateway policy.
- Traceability: Every change to the API spec instantly correlates with gateway updates.
- Auditability: Git history provides full accountability for versioned policy changes.
- Automation: Git triggers initiate CI/CD validation and deployment pipelines.
🚀 Step 3 — GitOps Deployment Pipeline
A Git push now drives the entire release process. Your pipeline validates, tests, and applies the configuration to staging or production environments automatically.
stages:
- validate
- deploy
validate:
script:
- spectral lint openapi.yaml
- deck validate kong.yaml
deploy:
script:
- deck sync --konfig kong.yaml
environment: production
- Spectral: Enforces design and naming rules in the OpenAPI spec.
- decK validate: Ensures Kong configuration integrity before sync.
- decK sync: Pushes validated configuration to the gateway, achieving true GitOps deployment.
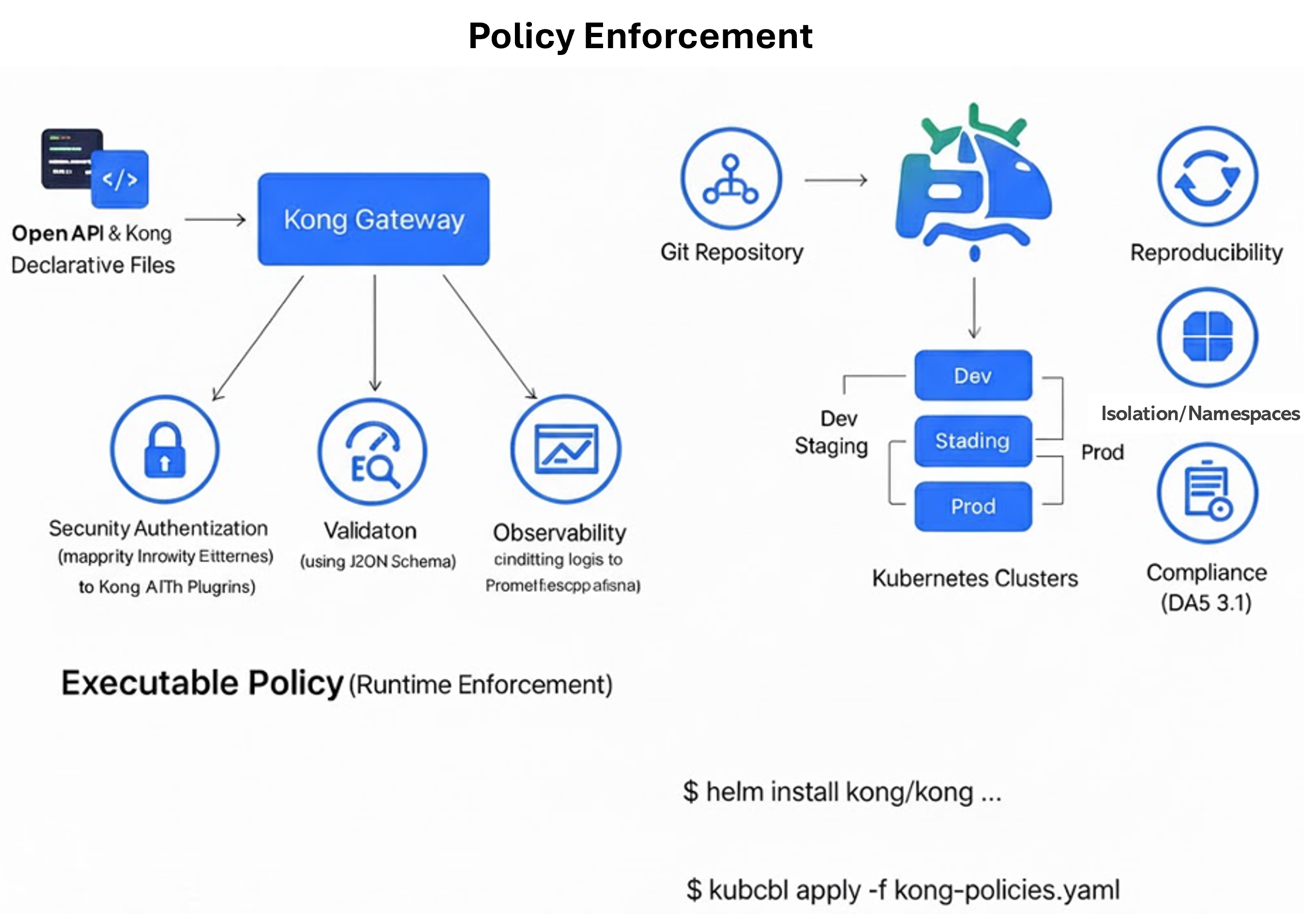
🔐 Step 4 — Policy-as-Code Enforcement
By combining OpenAPI and Kong declarative files, governance becomes programmable:
- Security: Enforce authentication via OAS
securitySchemes→ Kong auth plugins. - Validation: Use
request-validatorto ensure all inbound requests match your JSON Schema. - Rate Limiting & Quotas: Declaratively control consumption at the gateway layer.
- Observability: Stream logs and metrics to Prometheus / Grafana for continuous monitoring.
This transforms governance from a static document into executable policy, enforced continuously within your pipeline and runtime.
🧩 Step 5 — Integrating with Kubernetes & Helm
To scale across environments, deploy Kong Gateway as an Ingress Controller via Helm. Each cluster consumes your version-controlled Kong configuration from Git, ensuring environment consistency.
helm install kong kong/kong -f values.yaml
kubectl apply -f kong.yaml- Reproducibility: Every cluster enforces the same configuration state.
- Isolation: Namespaces represent different environments (dev, staging, prod).
- Compliance: All ingress and service routes follow centrally governed OAS 3.1 contracts.
📊 Step 6 — Continuous Validation and Monitoring
- OpenTelemetry Tracing: Attach tracing plugins to monitor API performance and latency.
- Prometheus Metrics: Export metrics to Grafana dashboards for live observability.
- Automated Drift Detection: decK diff reports any deviation between Git state and live Kong config.
deck diff --state kong.yaml --workspace prodThese continuous checks ensure your runtime always reflects the intended policy state — a closed feedback loop between design and operation.
🏁 Conclusion — From Blueprint to Execution
With this approach, your OpenAPI 3.1 specification becomes a living asset — defining, governing, and enforcing API behavior through every phase of the lifecycle. Combined with Kong Gateway, decK, and GitOps, you achieve true Policy-as-Code automation — where compliance, security, and scalability evolve at the same pace as innovation.
This completes the transition from theory to practice, bridging architecture and operations under the Ea-2-Sa vision of Design → Govern → Deploy. APIs are no longer static integrations — they are governed, observable, and continuously aligned with enterprise principles.